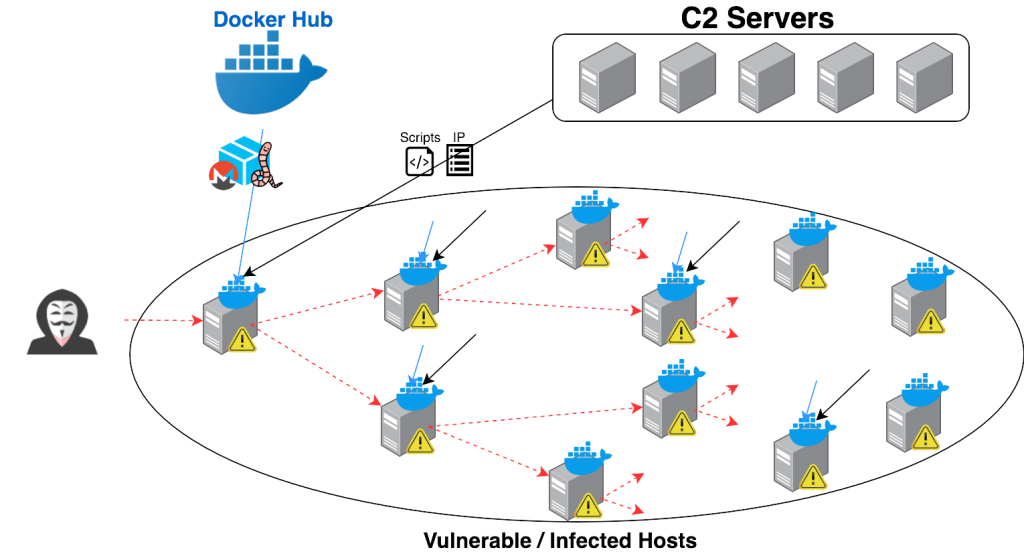
Named Graboid, the malware spreads into networks with an unsecured docking engine after a sandworm in the 1990 film “Tremors.” Docker containers are environments with a code and dependences provided by an application to operate on any supported infrastructure that are separated from the operating system. Searching for Shodan search engines, researchers at Palo Alto Networks find over 2,000 vulnerable Docker resources exposed to the public web. This is Graboid fodder. In their analysis the researchers found a Graboid control server script that found a list of over 2,000 IP addresses that the attacker has already scanned for vulnerable hosts. The number of people infected is unclear since the malware selects the next targets by chance from the list. When one has been compromised, the attacker sends remote commands to upload and deploy the “pocosow / centos” Docker image from Docker Hub. The picture is provided by the Docker client used to connect with other Docker hosts. The encryption operation (Monero) is conducted through a separate container called’ gakeaws / nginx.’ pocosow / centos’ is also used for downloading and executing four scripts from C2:
Live.sh-sends CPU information available on the affected host. Worm.sh-downloads the list of vulnerable hosts, selects new objectives and uses the Docker client to deploy’ pocosow / centos.’ Cleanxmr.sh-stops random host cryptomining operation. xmr.sh-Selects a random address from the list of compromised machines and deploys the’ gakeaws / nginx’ cryptomining container.
Palo Alto Networks noticed that Graboid receives commands from 15 compromised hosts, with 14 of these on the list of vulnerable IPs and the last one with over 50 known vulnerabilities, a clear indication that they were deliberately exploited for malware control purposes by the attacker. The two containers in Graboid Cryptojacking are downloaded thousands of times. The masker CenOS has more than 10,000 pulls and the Nginx has about 6,500 pulls.
Graboid actively tests new compromised hosts with a C2 database and uses the Docker software to install and distribute the infected container remotely.
Seeming Random Behavior
Unknown behavior evident Graboid follows an inconsistent trend, and the explanation remains unclear. Theories such as bad design, deception and conservation are all possible explications, according to the researchers in today’s paper. Each miner works approximately 60% of the time, and mining is limited to 250 seconds. In addition, miners don’t work at the same time, and even don’t begin the installation moment. “It randomly picks three targets at each iteration. It installs the worm on the first target, stops the miner on the second target, and starts the miner on the third target. This procedure leads to a very random mining behavior” – Palo Alto Networks Just put, compromised hosts on other infected hosts in the botnet monitor the mining process by instigating them to start or stop the session. In a simulation of the worm behavior, the researchers found that it takes around an hour for Graboid to spread to 1,400 infected Docker hosts. If each had one CPU, the botnet would always have a mining capacity of 900 CPUs. In the past there have been allegations of Cryptojacking activities involving Docker containers. A research from Juniper Networks in November last year found that cyber criminals were using the misconfigured Docker services to connect containers with the Monero mining script. Dofloo Trojan, a botnet known for launching DDoS attacks and Cryptomining, has been targeting mal-configured DevOps utility APIs during the summer.