During its assault on Mitsubishi Electric, Chinese hackers used zero days in the Trend Micro OfficeScan antivirus, ZDNet heard from similar sources. Trend Micro has now patched the flaw, but the firm has not reported on whether zero-day was used in any attacks besides Mitsubishi Electric. Click here to learn more about Trend Micro protection
MITSUBISHI ELECTRIC HACK
The Electric Hack Mitsubishi was launched this week on Monday. The Japanese computer manufacturer and defense contractor said it was compromised last year in a press release released on its website. On 28 June 2019, the organization said it found an attack into its network. After a long-term inquiry, Mitsubishi noticed that hackers got access to their internet from which they hacked about 200 MB of data. While the organization did not originally reveal the details of these records, in an amended press release, the company stated that the reports included more employee information rather than company business and partner data. The stolen documents included, according to Mitsubishi:
Employment application data for 1,987 persons Results of an 2012 employee survey filled out by 4,566 employees in their head offices Information on 1,569 employees in Mitsubishi Electric, who retired from 2007 to 2019 Confidential corporate technical materials, sales materials and others files.
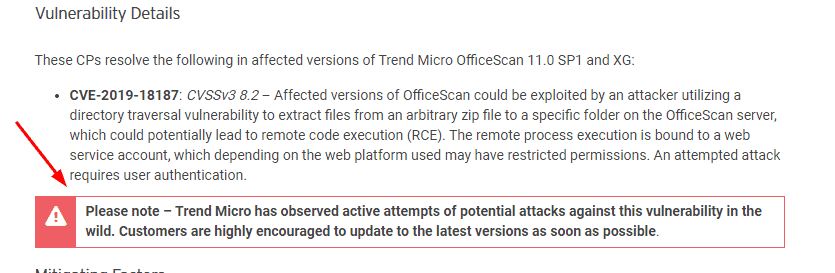
The Japanese media dug deeper into the breach this week. The hack was first developed by a Chinese subsidiary of Mitsubishi Electric and then expanded to 14 departments / networks of the organization. The intrusion is allegedly detected after a suspicious file is found on one of the servers of Mitsubishi Electric staff. The Japanese company verified none of this yet noticed Japanese reporters. The only technical detail about the attack was that hackers used a loophole in an anti-virus system used by Mitsubishi Electric. One person with the attack’s information informs the hackers targeted CVE-2019-18187, the Trend Micro OfficeScan antivirus ‘ cross-directory and arbitrary upload weakness. According to a protection advisory Trend Micro, which was delivered in October 2019, “OfficeScan infected variants could be used by an intruder who uses a transverse directory loophole to remove data from an arbitrary zip file to a different folder of the OfficeScan system, which can potentially lead to the remote code execution (RCE).” Once CVE-2019-18187 was fixed back in October, Trend Micro alerted consumers that hackers were involved in animals.
Japanese media reported that an attack was the product of a Chinese government-sponsored electronic espionage group called Tick. The Tick Cyber Group is known for launching several cyber operations in recent years for targets around the globe. It is currently unclear whether the organization used the OfficeScan zero-day against other goals as well.