The malware called Android / FileCoder. C by the ESET research team found to be targeting Android 5.1 or later devices. “Due to narrow targeting and flaws in both execution of the campaign and implementation of its encryption, the impact of this new ransomware is limited,” ESET’s researchers found. “After the ransomware sends out this batch of malicious SMSes, it encrypts most user files on the device and requests a ransom. Due to flawed encryption, it is possible to decrypt the affected files without any assistance from the attacker,” adds ESET. Nevertheless, if the ransomware developers succeed in revising their “product,” many Android users might face a very risky and potentially highly destructive strain of malware. Ransomware SMS infection FileCoder was seen by ESET during a campaign which lasted until 12 July and that the attackers distributed their malicious payload over messages posted on Reddit and on the mobile software development community of XDA Developers. While XDA has been deleted after notification, the Reddit threads have been released and released for FileCoder malware analysis by ESET malware researcher Lukas Stefanko. The developers of FileCoder distribute the ransomware with two servers, with malicious payloads connected to both malicious SMS messages sent to the full contact list of the victims, and to Reddit and XDA forum posts.
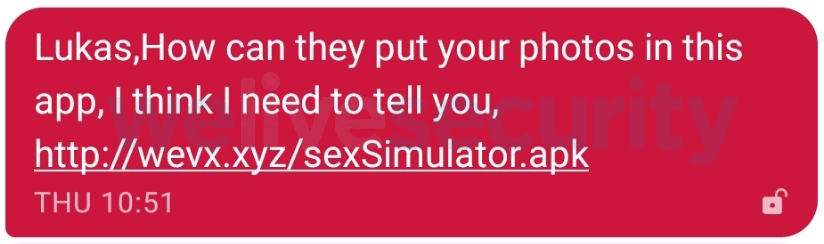
Malicious sms The ransomware samples are also connected with QR codes to speed up mobile users ‘ ability to install the malicious APK on their devices. In order to convince the potential victims to install the infected apps on their devices, operators of FileCoder would say that the app “allegedly uses photos of the potential victim.” However, the Reddit and XDA forums “promote” the malicious application as a free gender online game, which also reduces the potential targets ‘ guard to get them to download and install the ransom. Filecoder sample performs the below operation on execution “To maximize its reach, the ransomware has the 42 language versions of the message template […]. Before sending the messages, it chooses the version that fits the victim device’s language setting. To personalize these messages, the malware prepends the contact’s name to them,” ESET found. android.permission.WRITE_EXTERNAL_STORAGE android.permission.READ_EXTERNAL_STORAGE android.permission.READ_CONTACTS android.permission.RECEIVE_BOOT_COMPLETED android.permission.SEND_SMS android.permission.INTERNET
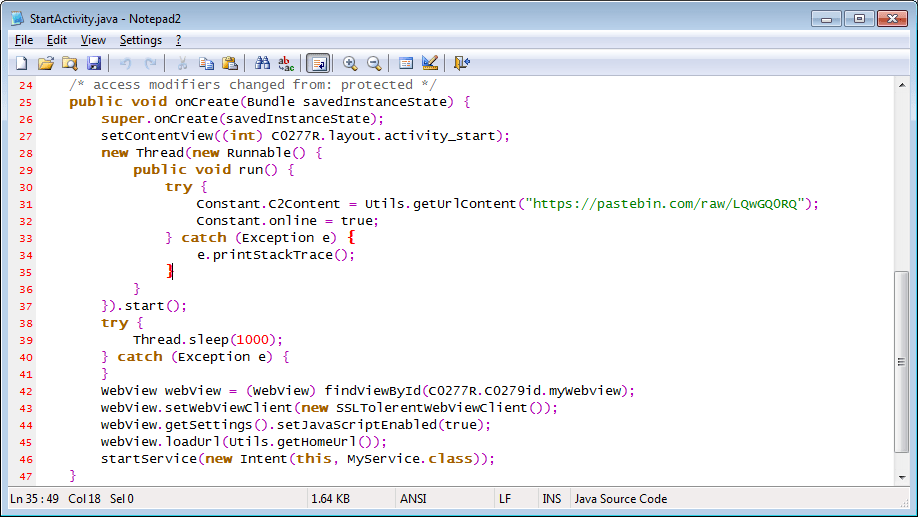
The FileCoder ransomware asks the victims to use a Bitcoin-ransomware, with the Bitcoin-addresses and the C2-server hardcoded in the sourcecode of the malware but with the option to send new addresses via the Pastebin service. FileCoder spreads over the contact list of the victims via SMS prior to the start of encrypting files in all directories on which the device can access, adding the extension.seven to the original file names — system files are skipped. “The ransomware also leaves files unencrypted if the file extension is “.zip” or “.rar” and the file size is over 51,200 KB/50 MB, and “.jpeg”, “.jpg” and “.png” files with a file size less than 150 KB,” adds ESET. The malware encrypts a strange mixture of Android file types and a weird combination of non-related document types. The ESET research team concludes, “The list is copied out of the notorious WannaCryptor alias WannaCry ransomware.”
Retrieving new C2 server domains & BTC addresses
FileCoder C2 servers still active
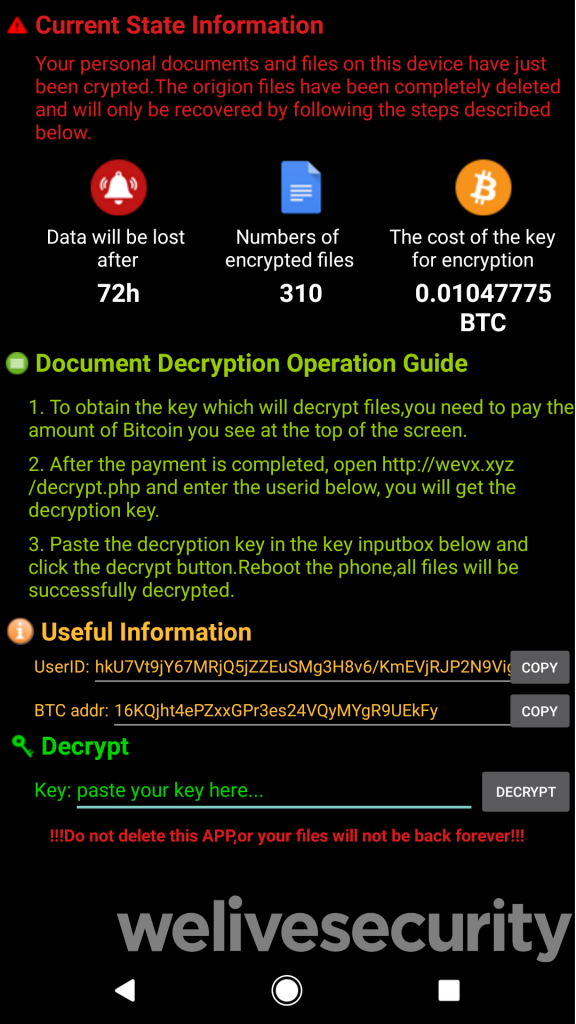
Once every file has been locked with the malware, the ransom note will show the number of encrypted files and the time the victim has to pay for the costs of the decryption key— ransom amounts range from $94 to $188. The ransom note states that if the ransom is not paid within three days, the data will be lost. “There is nothing in the ransomware’s code to support the claim that the affected data will be lost after 72 hours.”
FileCoder ransom note Unlike most ransomware strokes of Android, FileCoder does not lock the screens of victims and will allow them to continue using their devices, simply by wanting their files to be decoded as soon as possible. For each of the files it locks, FileCoder encrypts files using new AES keys, using a pair of public and private keys, which are encoded using the RSA algorithm. Since the developers of the Ransomware hardcoded the value used in the malware coding of the private key, however, victims could decrypt their data without paying for ransom. “All that is needed is the UserID [..] provided by the ransomware, and the ransomware’s APK file in case its authors change the hardcoded key value,” found the ESET researchers.FileCoder server The servers used by the authors of FileCoder were still available when this story was published, with the payment check page also available via one of the files hosting on the C2 server of the malware. Please contact us at our email address:h3athledger@yandex.ru. “The payment verification page also provides victims of a support email that they need to seek help if they face problems. At the end of Stefanko’s Filecoder Malware Analyses, further detailed information is provided on the interiors of the ransomware Android / Filecoder. C and a list of compromise indicators (IOCs) including malware sample hatching, the Bitcoin address used in a campaign.