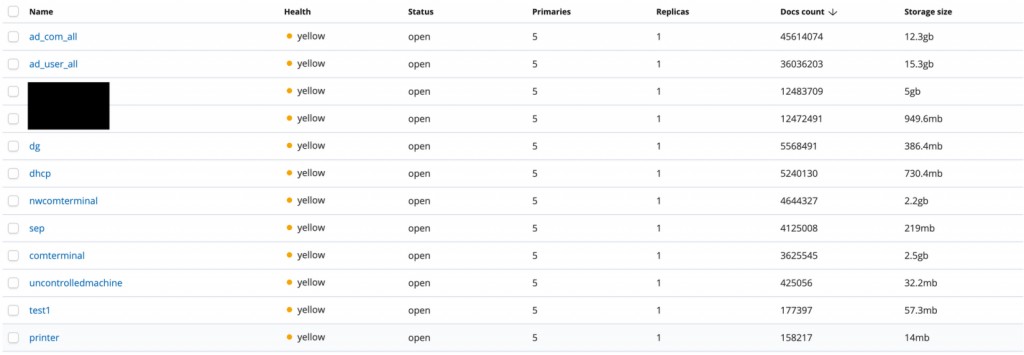
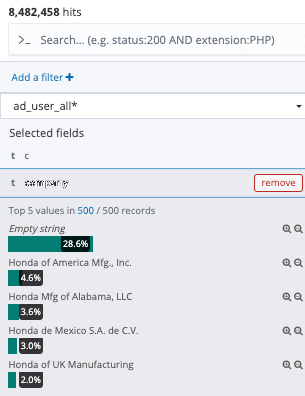
The ElasticSearch misconfigured database contains about 134 million documents with 40 GB of information for approximately 300,000 employees worldwide.
“The information available in the database appeared to be something like an inventory of all Honda internal machines,” says Justin Paine, the researcher who found the unsecured ElasticSearch instance. “This included information such as machine hostname, MAC address, internal IP, operating system version, which patches had been applied, and the status of Honda’s endpoint security software.”
About the Exposed Data
The unprotected ElasticSearch database revealed very specific data on hundreds of thousands of Honda employees like names and emails as well as on the network information, operating systems, OS versions, hostnames and patch status of your computer’s terminal security vendors. In addition, approximately 3,000 data points were stored in an’ uncontrolled machine’ table which is a list of Honda’s internal network computers that have not used a security device from the endpoint. The database also contained information on higher-value computers such as CFOs, CSOs and CEOs, which could enable attackers with sufficient knowledge to locate and access information they could use for highly targeted attacks. For instance, for a Honda CEO, the open database showed full name, account name, email and last log-in date, along with the computer’s “MAC address used by Windows KB / patches, OS, OS version, security endpoint status, IP, and device type.”
Database exposed
The data was updated daily, as it has discovered after analyzing database activity over 30 days, with approximately 40,000 new entries containing information about the Honda staff from around the world and their current network, security and OS status on their computers. Honda’s exposed database with a value of about three months starting on March 13 was founded by Paine on July 4th and after a few days of trying to find a contact to disclose his findings responsibly he was able to make contact on July 6th in the morning.
The database remained open for about six days as Shodan’s search for the discovery showed the time stamp of the discovery on 1 July 2019. Ten hours later, Honda secured the data and sent the following statement to the researcher for reporting the vulnerable database: “What makes this data particularly dangerous in the hands of an attacker is that it shows you exactly where the soft spots are,” concludes Paine. “I am specifically not going to name the major endpoint security vendor that protects Honda’s machines, but the data makes it clear which vendor they use and which machines have the endpoint security software enabled and up to date.”