Sphinx, a famous open source text search server, provides excellent indexing and information searching efficiency in databases or just files. It is accessible on a cross-platform basis, with Linux, Windows, macOS, Solaris, FreeBSD, etc.
Only local access
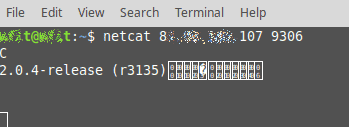
CERT-Bund today published on Twitter a warning alert network operators and suppliers of the danger of using a default web-based Sphinx server. The organisation points out that Sphinx does not have any authentication mechanisms. Exposing it on the internet allows an attacker to “read, alter or delete any information in the Sphinx database.” By default, the server is listening to 9306/TCP and 9312/TCP on all network interfaces. When searching one of the ports, Shodan returned a few thousand result, many of them with Sphinx servers. Administrators have a easy way to check whether their servers can be reached from the Internet using standard Linux / Unix tools. By operating’ netcat’ outside the local network from a laptop, admins can verify that a link can be formed. If so, they will see the server version data.
The suggestion of CERT-Bund shall not be to disclose Sphinx servers online and to prevent any link to its communication ports from the internet. Administrators can configure Sphinx for installations where Sphinx and the web server share the same machine to listen to the local interface. The advisory also includes the standard recommendation to operate Sphinx’s latest version. Many of the variants we saw on Shodan have been outdated.