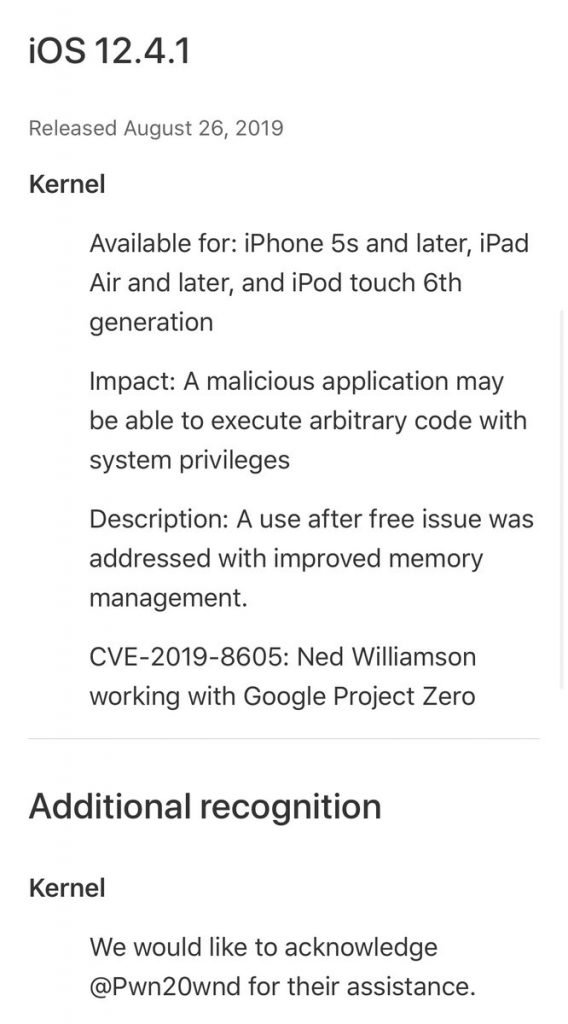
The today patched vulnerability of Apple is used after free tracking as the Sock puppet exploit of CVE-2019-8605, which was employed to create jailbreak tools for iOS devices. Google Project Zero’s Ned Williamson found the fault, earlier patched with Apple’s iOS 12.3 release on May 13, and now re-compared it to iOS 12.4.1. Apple acknowledges the contribution from the jailbreak developer As Apple’s support document outlining the safety of iOS 12.4.1 suggests, the bug could have been exploited by malicious applications that then could have been “capable of executing arbitrary code with system privileges.” Apple’s use following free security issues was tackled by introducing improved memory management, thereby blocking access to already freed pointers of maliciously crafted apps.
Apple recognized Google Project Zero’s contribution to Ned Williamson in identifying and resolving this safety problem and given extra appreciation for the help of Pwn20wnd. In addition to the fact that jailbreak developers can add assistance for Apple’s newest iOS variants, Apple’s flaw today also represents a critical vulnerability that could open the doors for attackers targeting the company’s bigiOS user base. Security researcher Stefan Esser also warned iOS users that once IOS 12.4 had been exploited byiOS jailbreak developers, anyone else could use the bug as well, with malicious iOS apps released through the Apple App Store. This safety update showed that Apple can react very rapidly to serious threats that expose its customers to possibly extremely harmful attacks while that was a big bug from Apple’s team.