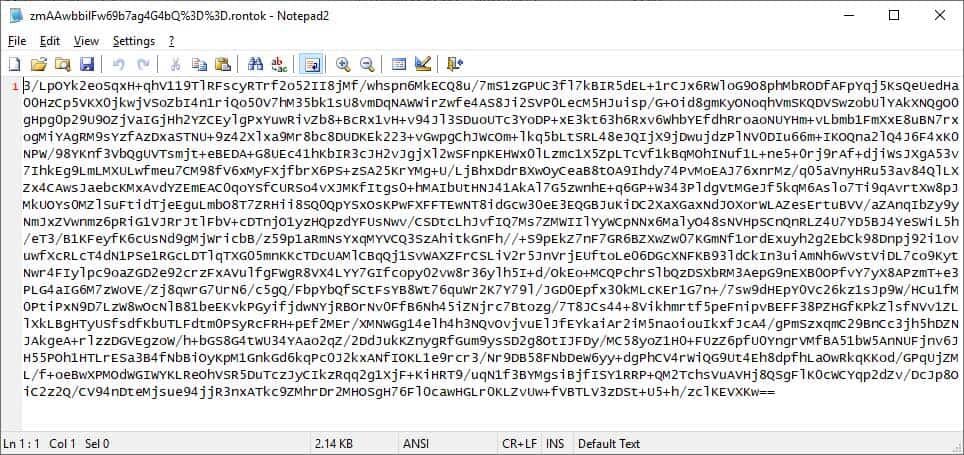
This encrypted website was running on Ubuntu 16.04 and all its files were encrypted, renamed and attached to them by the.rontok extension. Since a sample of the ransomware was not found, there is little other information than what we learned from the files submitted and the payment site. If B0r0nt0 K encrypts a file, it will base64 the encrypted data as shown below, according to Michael Gillespie. The name of the file will also be renamed by encrypting the file name, encoding it by base64, encoding it by url and finally adding the extension to the file name.rontok. An example of the name of an encrypted file is zmAAwbbilFw69b7ag4G4bQ%3D%3D.rontok
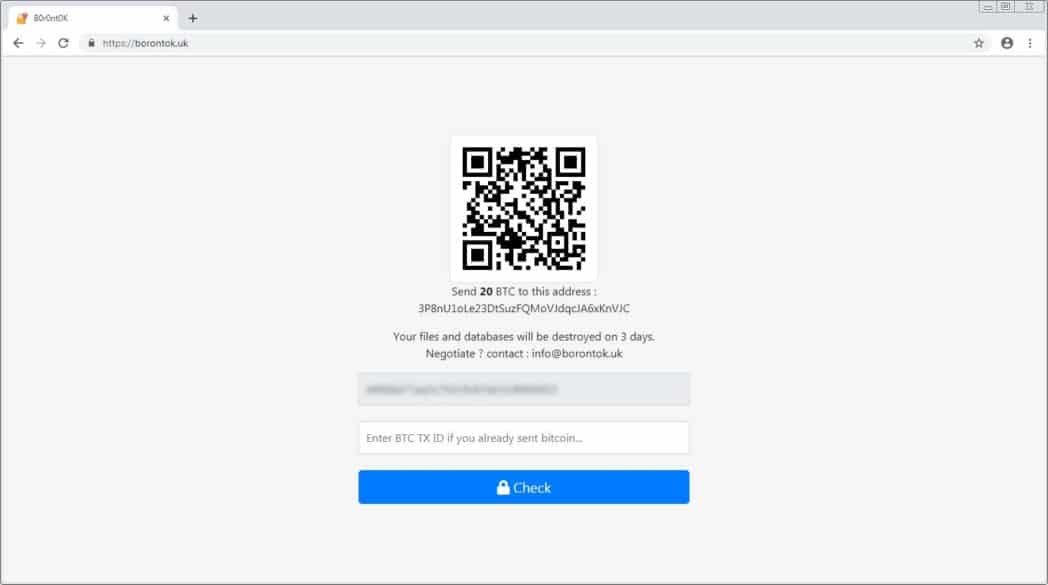
Although the user could not provide a ransom note, he could provide the payment site’s URL at https / borontok.uk. The user will be asked to submit his personal identification when visiting this site. Once an ID is entered, the user will receive a payment page that includes the amount of the bitcoin ransom, the bitcoin payment address and the email info@botontok.uk that can be used to contact the developers. The ransom demand in this particular case was 20 bitcoins, which is currently about $75,000. However, the developers seem willing to negotiate the price.
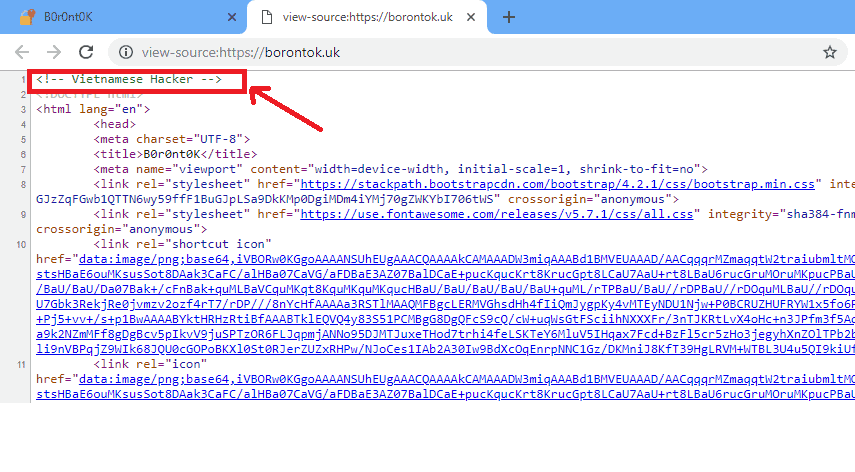
Also, anyone can see the hacker embedded comment “Vietnamese Hacker” when examining the source code for the payment site. Although this may indicate that the developer is Vietnamese, it is by no means proof.
Image credit: Bleeping Computers